A smart card authentication is a form of taking your data security level to a higher standard. It plays an important role in protecting your network and resources from malicious attacks. Next, let’s discuss the smart card authentication definition and importance. What authentication protocols can it use in a Windows Server 2003 environment? And what are its advantages and disadvantages?
Definition of Smart Card Authentication
Smart card authentication is designed to verify that users can use enterprise resources. Such as workstations and applications. It uses smart cards, smart devices, and authentication software to authenticate users. The enterprise can customize the access rights of the authenticated user in the back office. For example, what resources can be accessed and what actions can be performed on them.
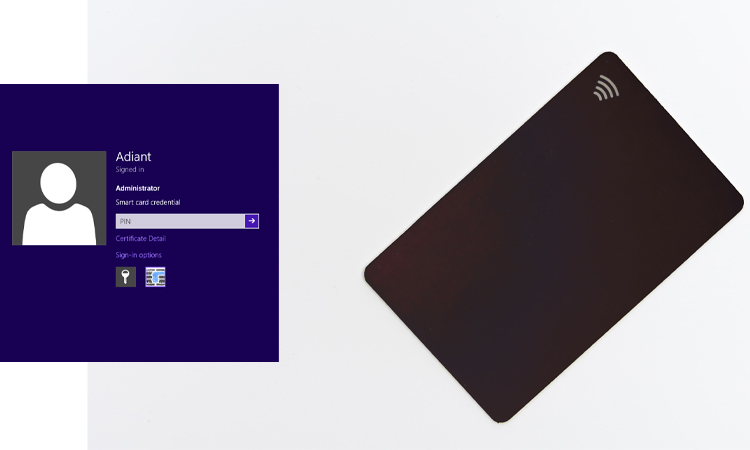
Platforms that support smart card authentication authenticate users through smart cards and PINs. The former is a storage device, storing the user’s public key credentials and PIN password. The latter is the key used by the system to authenticate the user’s identity.
Smart Card Authentication is a security system that utilizes a smart card to authenticate the identity of a user. A smart card is a plastic card that contains a microchip, which stores information and can be accessed by a reader. Smart card authentication is often used to secure access to physical locations, computer systems, and financial transactions.
The process for user authentication using smart cards is as follows:
- The enterprise associates the employee’s identity with the smart card. Smart cards store employees’ personally identifiable information and permissions.
- The employee inserts the card into a card reader connected to a workstation at the time of use.
- Authentication software allows employees to log in and use their resources after entering their PIN.
The above devices and software complement each other and cannot be used without one another. Without one of the above devices, users cannot access corporate resources.
Importance of Smart Card Authentication
Organizations need to verify the authenticity of users before providing them with services. Only after authentication is passed is the user allowed to access networks, systems, and applications. In particular, more organizations are choosing to store their data in databases. They allow their employees to access this data remotely. So there is a greater need for smart card authentication. And these user authentication mechanisms must also be tamper-proof. It is to prevent criminals from stealing organizational data.

The smart card reader authenticates each user’s smart card. Whenever users need to use data in the organization, they need to swipe their cards for authentication. They must swipe their smart card at the smart card reader and enter a specified PIN code. The reader applies many authentication factors in verifying the authenticity of that user.
Smart Card Authentication provides two-factor authentication for enterprises. Users need to pass swiped content (smart card) and a unique identifier (PIN) for that user to complete their authentication. This authentication method reduces the threat of endpoint data leakage in available databases.
Using Smart Card Authentication in Windows Server 2003
Authentication is the initial step users take to access network resources. Authentication in a Windows Server 2003 environment involves two processes. One is interactive login, and the other is network authentication. Interactive login occurs primarily when a user logs on to the system using a password or smart card. Network authentication occurs after the user has been granted access to a resource. This type of authentication eliminates the need for users to re-enter their passwords or PINs.
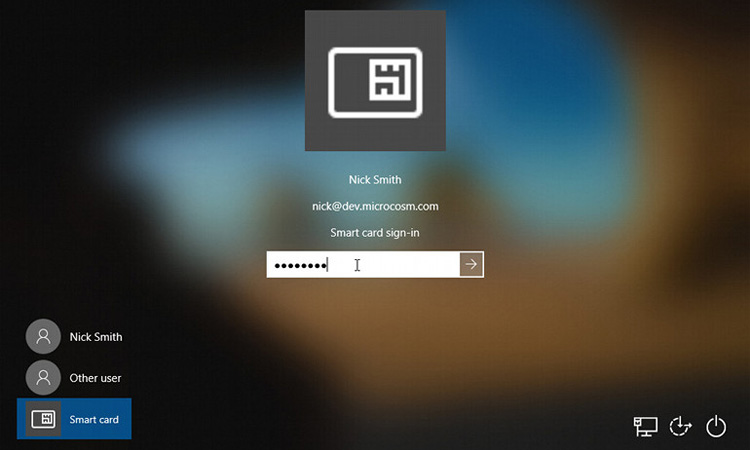
Users can confirm the authenticity of their identity by using a shared secret. The shared secret can be a password, an encryption key, or a secret PIN. Of course, sharing the secret has to happen on both sides. The two parties here are the user requesting authentication and their authenticator. In this way, authentication can be successful.
The sharing of secrets between users and authenticators also requires an authentication protocol. Only when the smart card authentication protocol is passed is the authenticator allowed access. Failure to authenticate will prevent further access to the network.
The following are some authentication protocols that can be used in a Windows Server 2003 environment:
- Kerberos version 5. This protocol can be used for network authentication in a Windows Server 2003 environment. You also use Kerberos version 5 for the interactive login authentication process.
- Secure Sockets Layer/Transport Layer Security (SSL/TLS). This protocol is based on X.509 public key certificates. SSL/TLS is mostly used for network authentication.
- Microsoft Windows NT LAN Manager (NTLM). This protocol is mainly used for Microsoft Windows NT 4 compatibility.
- Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2). Enterprises often use this protocol for network authentication and dial-up authentication. NTLM is also a protocol that can be used for network authentication.
- Password Authentication Protocol (PAP). This protocol is also one of the networks and dial-up authentication methods.
- Extensible Authentication Protocol-Transport Level Security (EAP-TLS). This protocol is a common way to authenticate wireless connections.
- Extensible Authentication Protocol (EAP). A protocol that can be used for network authentication and dial-up authentication. More typical examples are smart card support (hardware-enabled authentication).
For greater security, encryption keys are stored on smart cards and other encryption token mechanisms. It is because enabling authentication in hardware requires passing two requirements. Users need to have a smart card and PIN or password. The user can only access the system through this dual authentication. It means that smart card authentication provides a higher level of security for the enterprise. Any unauthorized individual accessing the system requires using a smart card and PIN.
As mentioned earlier, smart card authentication is a very useful authentication method. Users with a smart card also need to know the PIN to use it properly. A user needs to log in after entering the wrong PIN several times. You can cancel access to the smart card directly in the system. The presence of a smart card reader is quite important to enable these powerful features.
In Windows Server 2003, we recommend using a plug-and-play (PnP) reader. Smart cards have a microprocessor built into them and feature permanent flash memory. They can store the user’s login, private key, and other private information. To use a smart card reader, the user must insert the card into it and provide its PIN code. It allows the user to log in to the system successfully. Smart cards provide tamper-proof authentication for enterprises. There is a clear distinction between a smart card and a private software key. Smart cards allow you to move them from one mobile smart device to another.
You can usually connect these smart card readers to various computer ports. For example, a serial port, a USB port, or a PCMCIA port. PCs, laptops, and PDAs commonly used in everyday life have one of these ports. We use all computers to support smart card readers.
Most smart cards are like credit cards but come in many more forms. One of the more common ones is a dongle that plugs into a USB port. This connection is accessed by a cryptographic service provider (CSP). With the dongle access form, you do not need to have any special readers on hand. While this form of access is convenient, it is also expensive. The dongle form costs up to four times more than the traditional smart card form. A more advanced example is the magnetic smart card. Using these magnetic smart cards means they do not need an external link.
Advantages and Disadvantages of Smart Card Authentication
Smart card authentication offers an excellent option for organizations that value data security. It has many advantages that people can trust. Yet, it has some limitations.

Smart Card Authentication Benefits
- More security – Smart cards can give you a higher level of security than magnetic stripe cards. They often have a built-in microprocessor. It allows you to process data quickly without needing a remote connection. It is very difficult for criminals to delete, change or retrieve the data information stored on a smart card. So you don’t have to worry too much if your smart card falls into the hands of criminals. Criminals will have a hard time creating copies and cracking your database.
- More flexibility – Smart cards allow businesses to update their data information remotely. These smart cards are tamper-proof and cannot be copied. They are encrypted and have unique IDs, and users can access many services using smart cards. It means you can carry many separate cards on the go.
- Cheaper – Smart cards are usually made of plastic. They cost less and are cheaper than digital tokens and other identity verification platforms. In addition, they follow International Organization for Standardization (ISO) packaging standards. They can also pass International Electrotechnical Commission (IEC) packaging requirements.
- Higher processing power – The small CPU inside the smart card stores data and can do more. The CPU can count the number of times a user enters a PIN incorrectly. The CPU automatically locks out the user after many incorrect PINs are entered.
Smart Card Authentication Disadvantages
- Other devices are expensive – While smart cards are cheap, their readers are expensive. Therefore it is not suitable for investment by start-ups strapped for mobile capital.
- Low performance: Smart card authentication may not perform well in some infrastructure implementations. It is especially true in certain situations. For example, during the initial load, when users log in to their workstations. Therefore, you must meet the minimum hardware requirements when using smart card authentication.
- Easy to lose – Users can easily lose or damage their smart cards while using them. It is because these cards are lightweight and difficult to store. Using smart cards would be best to take relatively robust backup measures.
Smart Cards Types
There are two main types of smart cards: contact and contactless. Contact smart cards require physical contact with a reader to access the stored information. On the other hand, contactless smart cards use radio frequency identification (RFID) technology to transmit information to the reader without needing physical contact. Both types of smart cards offer high levels of security and are widely used in various industries.
Applications of Smart Card Authentication
Smart card authentication is used in various applications to secure access to information and physical locations. Some common examples include:
- Access control: Smart cards are often used to secure access to buildings, offices, and other physical locations. They can be programmed to grant or restrict access to certain areas based on the user’s permissions.
- Computer systems: Smart cards can secure access to computer systems and networks. This can be particularly useful in industries where sensitive information is handled, such as healthcare or finance.
- Financial transactions: Smart cards are also commonly used in financial transactions, such as point-of-sale systems or ATM transactions. They offer an additional layer of security to protect against fraud and unauthorized access to financial accounts.
What is a Smart Card?
A smart card is a relatively common type of security device. You can make it into a credit card-sized hardware token. Based on the use of smart cards, smart card authentication is supported in Windows 2000 and Windows Server 2003. Smart cards provide additional protection for most applications and security protocols.

Smart cards can provide enterprises with the following capabilities:
- Interactive login/administrator login/remote access login
- Secure code signing
- Secure email
- More secure user authentication methods
They are used in a network environment for the following purposes:
- Computer logins
- Encrypted emails
- Encrypted disk files (via EFS)
Smart card authentication is a good option for companies with high “data security” requirements. This dual layer of security greatly reduces the possibility of data leakage through the endpoint. Using this form of authentication, you can also ensure that the right users share the right resources.